Nowadays cybersecurity threats are becoming increasingly advanced and widespread, making it essential for enterprises to take a proactive approach to security. Continuous monitoring has become a cornerstone of current security measures, allowing for real-time identification of vulnerabilities and attacks.
This article helps you learn about the top 10 continuous monitoring tools, explaining their capabilities, use cases, and how they may improve your security posture. These technologies, ranging from refined commercial solutions to innovative open-source platforms, enable businesses to keep ahead of the ever-changing threat landscape.
What is Continuous Monitoring in Cybersecurity?
Continuous monitoring in cybersecurity involves constantly collecting, analyzing, and assessing data from an organization's IT systems, networks, and assets. Unlike periodic assessments, continuous monitoring ensures that risks are identified and mitigated in real time.
For example, continuous monitoring might detect unauthorized access attempts as they happen, allowing immediate action, whereas periodic assessments might only highlight such events after a scheduled review.
Key Components of Continuous Monitoring
- Real-time Data Collection: Combining logs, metrics, and traces from numerous sources to provide an extensive viewpoint. You may utilize tools like SigNoz to facilitate smooth data intake from dispersed systems, resulting in a unified view of logs, traces, and metrics. You may also use platforms such as Prometheus, which is primarily focused on metrics, whereas SigNoz mixes distributed tracing and metrics analysis, providing a broader perspective.
- Automated Analysis: Advanced algorithms and machine learning are used to correlate events and find abnormalities or possible risks. SigNoz includes a built-in query method for deep analysis, reducing the need for additional integrations. You may also utilize programs like Nagios, although they require substantial customization for equivalent functionality.
- Alerting and Reporting: Receive immediate notifications based on pre-defined criteria or discovered abnormalities, guaranteeing a quick reaction. SigNoz specializes in configurable alerting, allowing teams to prioritize according to effect and immediacy. You may also utilize Datadog, which has extensive alerting capabilities but is expensive for small-scale applications.
Importance of Real-Time Threat Detection and Response
Real-time threat detection is critical in minimizing the potential damage caused by security breaches. By identifying threats as they occur, organizations can:
- Mitigate risks before they escalate.
- Prevent prolonged exposure to vulnerabilities.
- Respond faster, reducing downtime and data loss.
For instance, a real-time monitoring system might flag unusual login patterns from different geographical locations, enabling teams to stop unauthorized access before sensitive data is compromised.
Difference Between Continuous Monitoring and Periodic Assessments:
While periodic assessments give a snapshot in time, continuous monitoring provides a real-time feed, allowing for speedier responses and minimizing the window of opportunity for attackers. This dynamic strategy is essential in today's fast-paced threat landscape.
Let’s see their differences.
| Aspect | Continuous Monitoring | Periodic Assessments |
|---|---|---|
| Timeframe | Real-time data collection and analysis | Snapshot of data at a specific point in time |
| Response Time | Immediate, reducing the window of opportunity for attackers | Delayed, based on review schedules |
| Threat Detection | Detects anomalies and threats as they occur | May miss threats that arise between assessments |
| Best Use Case | Dynamic environments with constant threat activity | Stable environments with lower risk profiles |
Why Continuous Monitoring Tools are Essential for Modern Security
Continuous monitoring tools are important to current cybersecurity measures. They provide not only visibility but also the capacity to respond quickly to emerging threats, ensuring a robust security posture.
- Rapid Detection of Security Incidents: Continuous monitoring tools enable the real-time detection of anomalies such as unexpected login attempts or traffic surges. For example, detecting unusual login attempts from unrecognized IPs or flagging a surge in outbound traffic indicative of data exfiltration.
- Enhanced Compliance With Regulatory Requirements: Meeting requirements such as GDPR, HIPAA, or ISO 27001 frequently requires enterprises to monitor systems for compliance regularly.
- Enhanced Visibility into Network and System Activities: Detailed visibility into system behaviour aids in the detection of subtle security breaches, such as odd traffic patterns or unauthorized access attempts. You can use tools like Splunk for log analysis or Prometheus for network metrics can provide actionable insights.
- Proactive Risk Management and Threat Mitigation: Continuous monitoring tools assist detect and address vulnerabilities before they are exploited.
Why Modern Threats Require Proactive Tools
As the use of cloud services, IoT devices, and remote work arrangements increases, continuous monitoring technologies become increasingly important in fighting against advanced persistent threats (APTs) and ransomware.
Top 10 Continuous Monitoring Tools for 2024
Let's now take a look at the top 10 continuous monitoring tools.
1. SigNoz
SigNoz stands out as an innovative, open-source application performance monitoring (APM) tool intended for easy integration with distributed systems. SigNoz, based on OpenTelemetry, provides detailed insights into application performance via distributed tracing, metrics analysis, and logs.
Key Features
- Distributed Tracing: Visualize the complete lifecycle of requests across services for faster debugging.
- Custom Dashboards: Easily construct dashboards that are specific to your organization's monitoring requirements.
- Built-in Metrics Storage: SigNoz eliminates the need for external storage systems such as Prometheus, which simplifies infrastructure administration.
Use Cases
- A microservices-based e-commerce platform employs SigNoz to identify the source of latency during high-traffic events like flash sales.
- Troubleshooting difficulties in multi-region deployments by visualizing dispersed traces to pinpoint bottlenecks in certain regions.
Limitations
- In contrast to plug-and-play tools, initial configuration and setup are required.
- To properly utilize some sophisticated functions, further experience may be required.
Example Use Case
Assume you're running a microservices-based e-commerce application where response latency increases during flash sales. Using SigNoz:
- Distributed traces can identify the specific service causing the delay.
- Metric dashboards help identify bottlenecks in database queries.
- Alerting systems can warn engineers when thresholds are exceeded, allowing for prompt response.
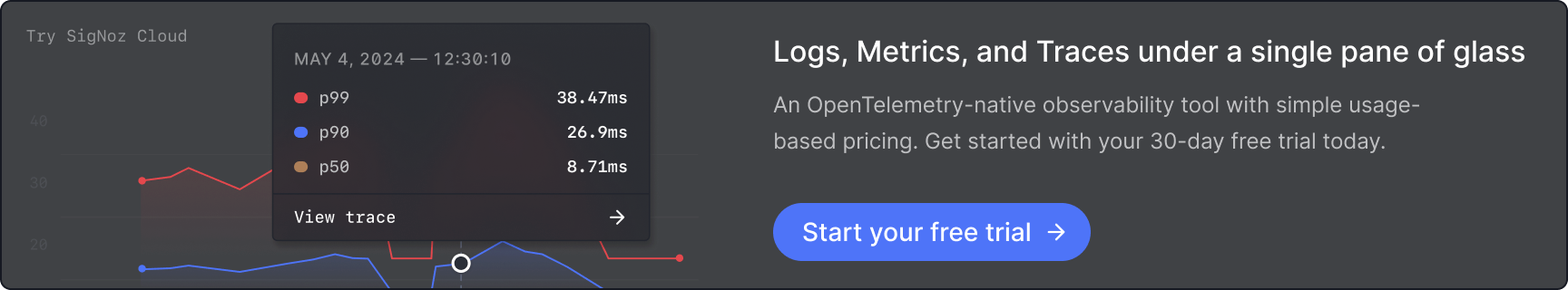
Visualizing Distributed Traces in SigNoz
Splunk remains the market leader in real-time log management and analytics, making it essential for businesses managing complex IT infrastructures.
Key Features
- Machine Learning Capabilities: Automatically detects anomalies and predicts potential system failures.
- Customizable Dashboards: Provides rich visualizations for log data, making it easier to identify trends.
- Data Integration: Seamlessly integrates with third-party tools and supports massive data ingestion.
Use Cases
- A global bank utilizes Splunk to monitor financial transactions and detect fraudulent activity in real time.
- IT personnel in a retail company use Splunk to analyze website logs, assuring peak performance during peak shopping seasons.
Limitations
- The high license costs make it unsuitable for small firms. Additionally, teams inexperienced with complex log query methods, such as Splunk's Search Processing Language (SPL), may face a steeper learning curve.
3. Qualys Continuous Monitoring
Qualys excels in providing real-time security monitoring and vulnerability management for enterprise networks.
Key Features
- Comprehensive Asset Discovery: Scans networks to detect all connected devices and vulnerabilities.
- Proactive Alerts: Sends quick notifications of unauthorized access or new vulnerabilities.
- Compliance Readiness: Ensures compliance with standards like as ISO 27001, HIPAA, and PCI DSS.
Use Cases
- A healthcare institution employs Qualys to check that medical devices are secure and comply with regulatory criteria.
- A multinational organization uses Qualys to detect and fix vulnerabilities in multi-cloud environments.
Limitations
- Can provide a high amount of false positives, increasing the strain on security staff.
- Cloud-based scanning requires high-quality internet connectivity.
4. Datadog
Datadog is popular among DevOps teams because it offers a comprehensive solution for infrastructure monitoring, application performance management (APM), and log management.
Key Features
- Unified Monitoring: Combines infrastructure metrics, application traces, and logs into a single platform.
- AI-Powered Insights: Identifies performance bottlenecks and predicts system failures.
- Seamless Integration: Supports over 450 integrations with popular tools like Kubernetes, AWS, and Docker.
Use Cases
- A SaaS firm uses Datadog to track the performance of containerized microservices in production.
- During sales campaigns, an e-commerce platform will use it to identify and address database query bottlenecks.
Limitations
- Enterprises with large infrastructures may incur high costs.
- Excessive data collecting might overload teams in the absence of suitable filters and alarm thresholds.
5. Nagios
Nagios has long been a trusted brand in infrastructure and network monitoring, known for its robust plugin ecosystem and dependability.
Key Features
- Extensive Plugin Ecosystem: Monitor everything from servers to applications using community-contributed plugins.
- Flexible Notification Options: Alerts can be sent via email, SMS, or third-party integrations.
- Performance Graphing: Provides historical insights into resource utilization trends.
Use Cases
- A web hosting company utilizes Nagios to monitor uptime across several data centres, ensuring SLAs are satisfied.
- IT administrators in small and medium-sized enterprises use Nagios to monitor important services such as DNS and HTTP.
Limitations
- Manual configuration may be time-consuming for larger infrastructures.
- There is little support for contemporary, dynamic architectures like as containers and serverless systems.
6. Prometheus
Prometheus is a popular open-source tool that is ideal for monitoring containerized and cloud-native systems.
Key Features
- Time-Series Database: Ideal for storing high-resolution metrics from dynamic environments.
- Powerful Query Language (PromQL): Enables complex queries to derive actionable insights.
- Built-In Alert Manager: Automatically notifies teams of issues in real-time.
Use Cases
- A DevOps team uses Prometheus to monitor Kubernetes clusters, measure pod resource utilization, and scale services as needed.
- Gaming firms utilize Prometheus to monitor real-time user metrics like active players and server response times.
Limitations
- No built-in long-term storage option, necessitating integration with programs such as Thanos for longer retention.
- Dashboarding capabilities are limited when compared to tools such as Grafana.
7. BitSight
BitSight is known for managing third-party cyber risks, providing visibility into vendor security and external attack surfaces.
Key Features
- Risk Assessment Scoring: Provides an easy-to-understand score for vendor and partner risks.
- Attack Surface Visibility: Tracks and evaluates your organization’s exposure to cyber threats.
Use Cases
- A logistics business uses BitSight to evaluate the cybersecurity posture of its supply chain partners.
- Government agencies utilize BitSight to guarantee that contractors fulfil minimum security standards before onboarding.
Limitations
- Concentrates mostly on third-party hazards, with minimal capability for internal system monitoring.
- Expensive for enterprises with large third-party networks.
8. CrowdStrike Falcon
CrowdStrike Falcon excels at endpoint detection and response (EDR), making it an excellent choice for current cybersecurity organizations.
Key Features
- Behavioral Analytics: Detects high-level threats by identifying patterns of harmful activity.
- Real-Time Threat Intelligence: Consistently updated with the most recent information on global threats.
- Lightweight Agents have minimal impact on device performance.
Use Cases
- A software business utilizes CrowdStrike to safeguard employee laptops against ransomware attacks.
- Financial institutions use CrowdStrike to protect high-value endpoints against phishing attempts.
Limitations
- Endpoints are the primary focus, with minimal visibility into the network infrastructure.
- Premium features can dramatically increase pricing.
9. Lansweeper
Lansweeper specializes in asset management and IT inventory tracking, ensuring enterprises have complete visibility into their IT landscape.
Key Features
- Device Discovery: Automatically detects all linked devices across networks, including servers, workstations, and IoT devices.
- License Monitoring and Compliance: Lansweeper scans installed software across all systems, cross-referencing licenses to ensure compliance. It identifies unused licenses to optimize costs and flags instances of non-compliance by comparing current usage against permitted terms.
Use Cases
- A hospital manages inventories for key medical devices using Lansweeper, assuring uptime and compliance.
- A technology company uses Lansweeper's reporting functions to keep track of IT asset depreciation.
Limitations
- Limited real-time monitoring compared to other technologies.
- Best suited to static environments; less effective in dynamic cloud architectures.
10. Monit
Monit is a lightweight monitoring tool ideal for small-scale setups, providing essential features without unnecessary complexity.
Key Features
- It automatically restarts failing services or processes.
- It notifies admins of system issues via email or SMS.
Use Cases
- A small business uses Monit to monitor server uptime and restart services when they fail, preventing revenue losses caused by prolonged downtime of their e-commerce platform.
- IT teams in startups deploy Monit to ensure basic health checks for critical applications. For instance, if a database service crashes unexpectedly, Monit detects the failure and restarts the service automatically, avoiding disruption to ongoing user transactions.
Limitations
- Lacks strong analytics and visualization capabilities.
- Scalability is limited for larger or more complicated infrastructures.
How to Implement Continuous Monitoring Effectively
To get the most out of continuous monitoring tools, you can follow these steps.
- Identify critical assets and systems to monitor.
- Start by mapping out your organization's core systems and applications.
- For an e-commerce website, prioritize payment gateways, databases, and customer-facing services.
- Define Key Performance Indicators (KPIs) and Metrics.
- Select metrics that are relevant to your company objectives, such as latency, error rates, or CPU utilization.
- For example, use measures like '99.9% uptime' and ‘response times under 200ms' to assess customer satisfaction.
- Establish Baseline Behavior for Normal Operations
Collect data over a defined period to understand normal performance patterns.
Diagram Example:
4. Develop and Test Incident Response Procedures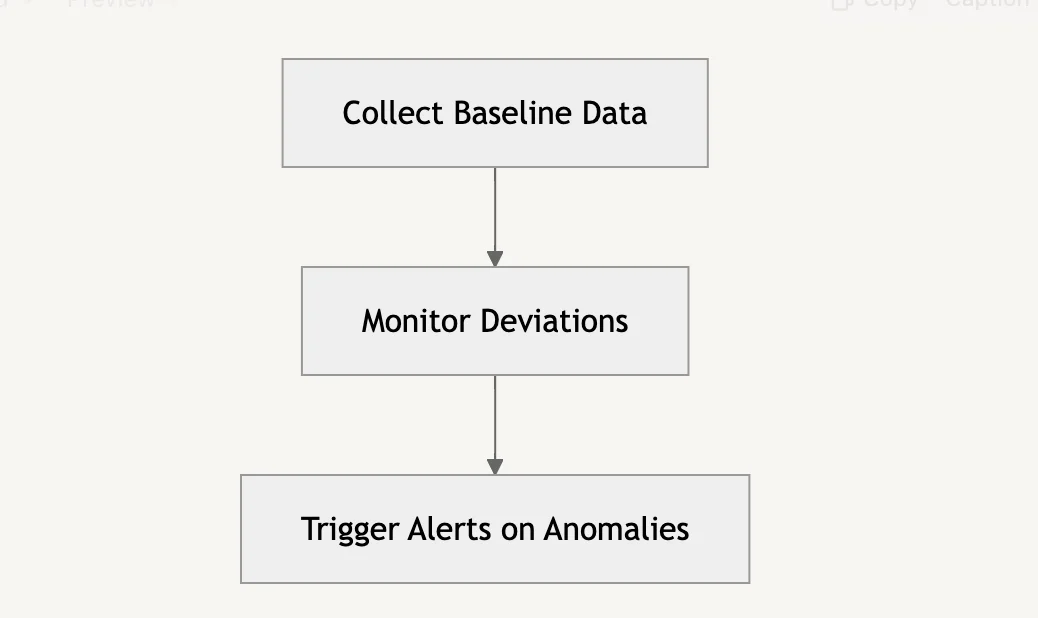
Create a step-by-step strategy for managing alarms to reduce downtime.
For example, simulate DDoS attacks to fine-tune response methods.
- Conduct regular reviews and updates to monitoring strategies
- Evaluate and change plans regularly to deal with evolving threats.
- For example, integrate new tools or KPIs in response to corporate expansion.
Pro Tip: Effective implementation necessitates an iterative approach; tweak and adjust as you go.
Overcoming Challenges in Continuous Monitoring
1. Data Overload
- Challenge: Managing large data volumes can overwhelm storage and processing systems.
- Solution: Use SigNoz or Prometheus for efficient data aggregation and visualization.
- Example: Use data filters to focus primarily on high-impact metrics.
2. Alert Fatigue
- Challenge: Excessive notifications can make teams less sensitive to key situations.
- Solution: Configure alerts with appropriate thresholds to reduce false positives.
- Example: Only send CPU use alerts when it surpasses 80% for five minutes.
3. Data Privacy
- Challenge: Monitoring may unintentionally collect sensitive information.
- Solution: To ensure data security, use role-based access controls (RBAC) and encryption.
4. Tool Integration
- Challenge: Using different tools can result in fragmented monitoring.
- Solution: Choose technologies with comprehensive APIs and prebuilt integrations (e.g., SigNoz and Datadog).
5. Skill Gaps
- Challenge: Teams may lack competence in managing advanced monitoring tools.
- Solution: Invest in skill development and certification.
Pro tip: Overcoming such challenges makes sure your monitoring strategy remains robust and effective.
| Challenge | Solution | Example |
|---|---|---|
| Data Overload | Use tools like SigNoz for efficient data aggregation and visualization. | Use data filters to focus primarily on high-impact metrics. |
| Alert Fatigue | Configure alerts with appropriate thresholds to reduce false positives. | Send CPU use alerts only when it surpasses 80% for five minutes. |
| Data Privacy | Ensure data security using role-based access controls (RBAC) and encryption. | Avoid storing sensitive data in plain text. |
| Tool Integration | Choose technologies with comprehensive APIs and prebuilt integrations (e.g., SigNoz, Datadog). | Centralize data collection using integrated dashboards. |
| Skill Gaps | Invest in skill development and certification. | Provide training sessions on monitoring tools. |
SigNoz: A Comprehensive Solution for Application Monitoring
SigNoz is an application monitoring solution that simplifies contemporary tech stacks by providing end-to-end distributed tracing to understand request flows across microservices.
- Real-time Metrics and Log Analysis: Get actionable insights quickly.
- Custom Dashboards and Alerting: Create monitoring views tailored to specific use scenarios.
- Easy Deployment and Scalability: Choose from self-hosted or managed solutions.
SigNoz cloud is the easiest way to run SigNoz. Sign up for a free account and get 30 days of unlimited access to all features.
You can also install and self-host SigNoz yourself since it is open-source. With 19,000+ GitHub stars, open-source SigNoz is loved by developers. Find the instructions to self-host SigNoz.
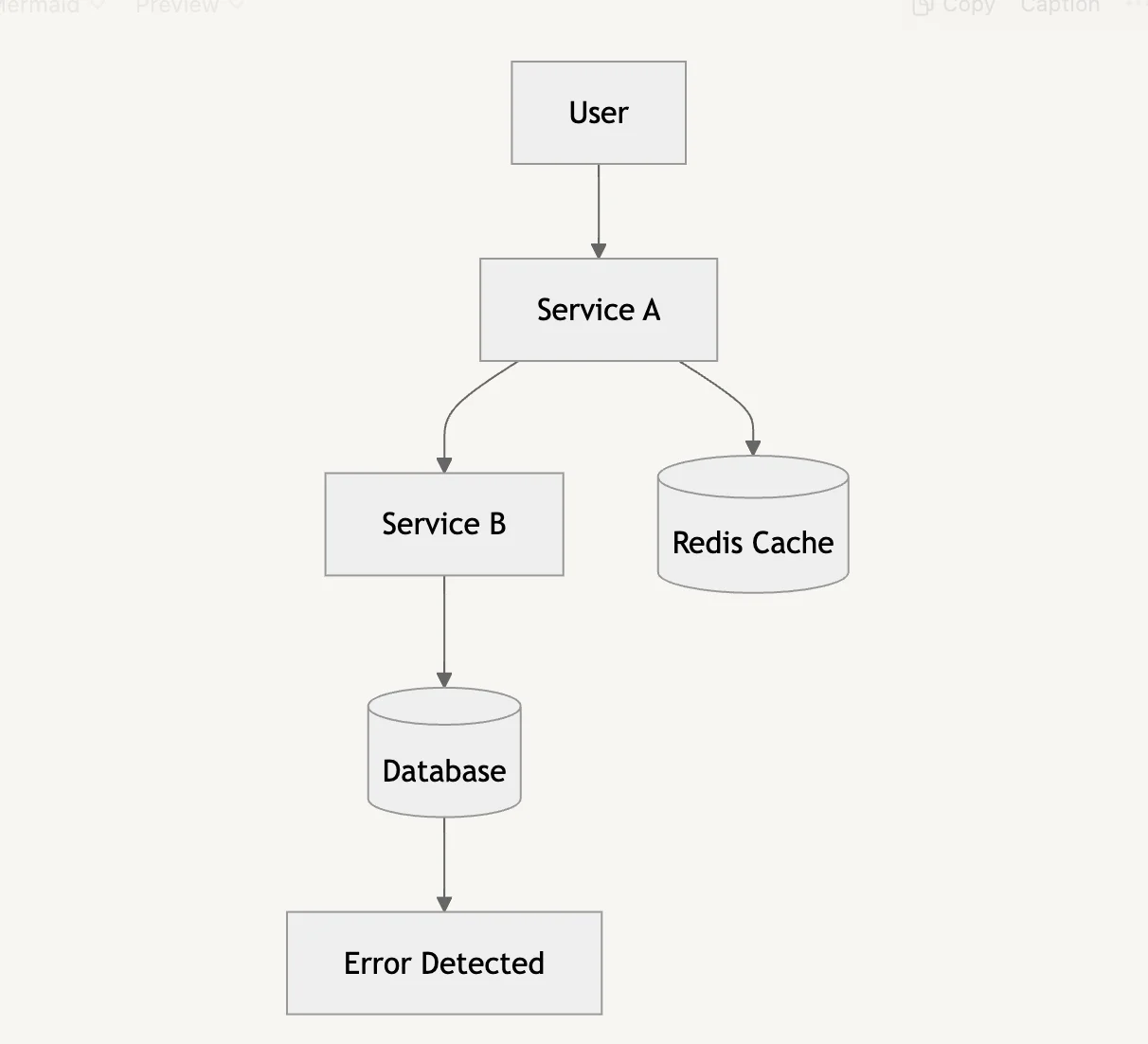
Example Architecture: Monitoring Microservices with SigNoz
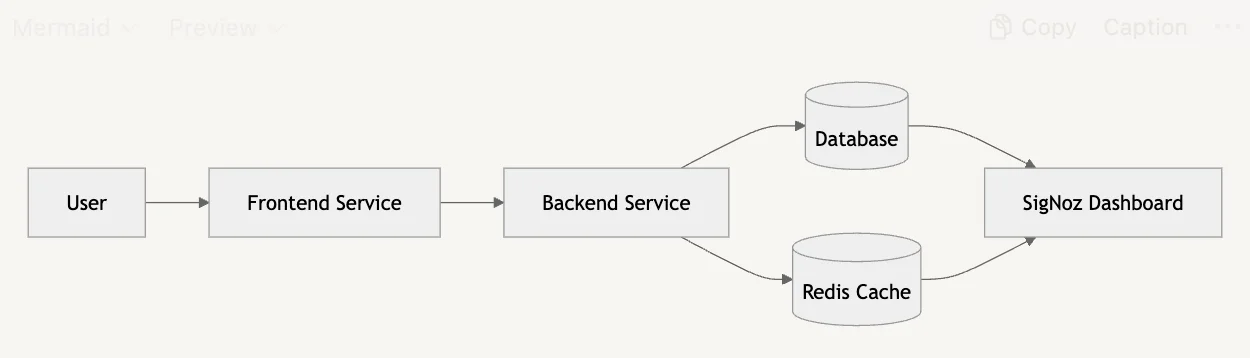
- Implement a Layered Security Approach
- Continuous monitoring is most effective when paired with additional security measures, including firewalls, intrusion detection systems, and endpoint protection solutions.
- For example, use monitoring tools such as SigNoz and CrowdStrike Falcon to track threats at both the application and endpoint levels.
- Prioritize Alerts Based on Risk
- Not every alert requires equal attention. Use risk-based prioritizing to prioritize the most important items first.
- As an example, set severity levels:
- High severity: Unauthorized access attempts or critical service disruptions.
- Medium severity: Multiple unsuccessful login attempts.
- Low severity: routine system updates.
- Automate Response Actions
- Automating repetitive activities saves time and reduces human error.
- For example, use Ansible or AWS Lambda to automatically scale up resources when CPU consumption exceeds a certain threshold.
- Another example is to restart a failing service in a Kubernetes pod using pre-defined scripts.
- Conduct regular training
- Conduct regular training to equip your team with knowledge of tools and emerging dangers.
- For example, hold quarterly workshops on using tools like Splunk or Prometheus for real-time data visualization and alerting.
- Continuously Update Monitoring Rules
- Regularly update regulations to reflect new technologies, procedures, and cyber dangers.
- For example, if you're shifting to a microservices architecture, start monitoring API request rates, latencies, and errors.
- Integrate Monitoring into DevOps Pipelines
- Include monitoring tools early in the development process to identify potential issues during deployment.
- Collaborate Across Teams
- Encourage communication across development, operations, and security teams to improve monitoring efficiency.
Pro Tip: Review your plan semi-annually to verify it is in line with business goals and compliance needs.
Key Takeaways
- It provides real-time visibility into system health and performance, allowing proactive problem solutions.
- Choose tools that are appropriate for your organization's size, infrastructure, and security needs. For example, Nagios is appropriate for small teams, whereas Splunk is appropriate for large organizations.
- Automate mundane processes and make sure your tools are scalable with your infrastructure. Open-source technologies, such as SigNoz, allow for cost-effective scaling.
- Regularly update your monitoring rules and methods to keep up with changing security threats.
- While automation increases productivity, human oversight is required for sophisticated decision-making and handling edge cases.
- Address challenges such as alert fatigue with intelligent alerting systems, and train your team to successfully use monitoring technologies.
FAQs
What is the difference between continuous monitoring and SIEM?
Continuous monitoring delivers real-time insights into your infrastructure, allowing for preemptive detection of performance and security issues. SIEM systems, on the other hand, examine previous log data from different sources, connecting events to discover potentially existing incidents.
- For example, continuous monitoring detects real-time CPU spikes, whereas SIEM analyzes log patterns to identify potential threats such as brute-force attacks.
- Both are complementary; continuous monitoring is proactive, whereas SIEM is investigative.
How frequently should I examine my continuous monitoring strategy?
You should assess your monitoring approach quarterly at the least, or anytime substantial changes occur in your IT environment, such as:
- Infrastructure updates (such as cloud migration or containerization).
- New regulatory obligations (such as GDPR and HIPAA).
- Emerging dangers (such as zero-day vulnerabilities).
Frequent reviews Ensure your monitoring system remains effective and aligned with organizational goals.
Can continuous monitoring tools replace traditional security measures?
No, continuous monitoring technologies are not a replacement, but rather an addition to established procedures.
- Firewalls and antivirus software defend against known dangers.
- Continuous monitoring detects unexpected activity that other measures may overlook, such as insider threats or misconfiguration.
What are the potential drawbacks of continuous monitoring?
While continuous monitoring is essential, it does have challenges:
- High Initial Costs: Advanced technologies such as Splunk or Datadog necessitate a large investment in setup and licensing. Mitigation: For cost efficiency, use open-source technologies such as SigNoz.
- Skill Gaps: Teams may lack the knowledge to configure and evaluate monitoring data. Mitigation: Regular training and certifications might help close the gap.
- Alert Fatigue: A constant barrage of notifications can de-sensitize teams, causing vital issues to be overlooked. Mitigation: Use intelligent alerts and prioritize according to severity.
- Data Privacy Concerns: Monitoring tools may mistakenly disclose sensitive information. Mitigation: Encrypt data and use role-based access controls.